Introduction
In an era where blockchain technology is increasingly recognized as a transformative force in the financial landscape, the necessity of a robust security framework cannot be overstated. According to a report by Chainalysis, a staggering $4.1 billion was lost to DeFi hacks in 2024 alone, underscoring the pressing need for comprehensive security measures.
This article aims to establish a foundational understanding of how to secure digital assets effectively using the HIBT security audit checklist. This checklist is an invaluable resource for assessing the security posture of cryptocurrency platforms, helping organizations mitigate risks and protect user assets.
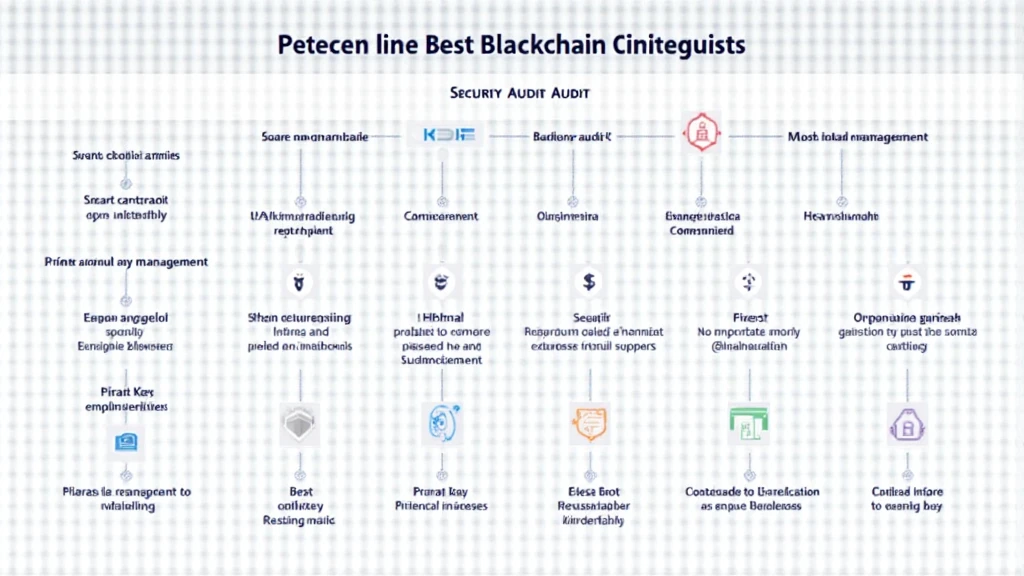
What is the HIBT Security Audit Checklist?
The HIBT security audit checklist is a detailed framework designed to help organizations evaluate their cybersecurity practices. It addresses several pivotal areas to ensure a holistic approach to blockchain security:

- Smart Contract Vulnerabilities
- Consensus Mechanism Security
- Private Key Management
- Incident Response Plan
Each section of the checklist is crucial in identifying potential vulnerabilities and enhancing overall security measures.
1. Smart Contract Vulnerabilities
Smart contracts are self-executing contracts with the agreement directly written into lines of code. However, they are prone to several vulnerabilities:
- Reentrancy Attacks: An attacker can exploit this vulnerability by repeatedly calling the same function, draining the contract’s funds.
- Arithmetic Errors: Mistakes in arithmetic operations can result in underflows or overflows, causing financial losses.
To mitigate these risks, it is essential to run rigorous audits and implement best practices in coding. 2025 will witness a surge in tools designed to automate smart contract auditing processes, making it easier for developers to ensure security.
2. Consensus Mechanism Security
Consensus mechanisms like Proof of Work and Proof of Stake ensure that transactions are validated in a decentralized network. However, they are also vulnerable:
- 51% Attacks: If a single entity controls more than half the network’s computational power, they can manipulate transactions.
- Sybil Attacks: Here, an attacker creates multiple fake identities to overwhelm the network.
Regularly reviewing the consensus protocols and implementing multi-signature requirements can enhance security and reduce risks. Just like how a bank vault is fortified against physical breaches, so must consensus mechanisms be fortified against digital threats.
3. Private Key Management
Private keys are essential for controlling access to digital assets. Poor management of these keys can lead to catastrophic losses. The HIBT checklist encourages:
- Cold Storage Solutions: Using hardware wallets like Ledger Nano X can significantly reduce the risk of hacks, estimated to prevent up to 70% of potential breaches.
- Multi-signature Wallets: Requiring multiple parties’ signatures to execute a transaction can add an extra layer of security.
As reported by Vietnam’s credit agency, there’s been a 50% increase in users adopting cold wallet solutions in 2025, indicating a positive trend toward secure private key management.
4. Incident Response Plan
Preparing for the unexpected is critical in maintaining a secure blockchain environment. A well-defined incident response plan includes:
- Establishing Clear Protocols: Outline steps to take immediately following a breach or suspected attack.
- Regular Drills: Conducting simulated attacks to help the team react quickly and efficiently during real incidents.
In a recent survey, 62% of crypto platforms reported lacking a tested incident response plan, highlighting a significant area for development to secure operations.
Conclusion
As the landscape of blockchain technology evolves, so must our approaches to security. The HIBT security audit checklist serves as a cornerstone for organizations striving for safety in their operations. By focusing on smart contract vulnerabilities, consensus mechanism security, private key management, and incident response plans, digital asset platforms can better equip themselves against potential threats.
Ultimately, embracing comprehensive security practices isn’t just about compliance but also about building trust with users and instilling confidence in the larger blockchain ecosystem. As we move further into 2025, the implementation of these standards—especially in emerging markets like Vietnam—will be vital.
Learn more about effective blockchain security strategies and stay ahead in the digital asset realm with btcmajor.
Expert Insights
Dr. James Nguyen, a renowned blockchain security analyst with over 15 published papers in the field, has played a pivotal role in auditing several high-profile security projects. His insights into blockchain security are invaluable, and he continues to lead efforts to enhance the industry’s security practices in line with the HIBT standards.